Security
Phishing mails getting more clever
01.07.16
This is the second time I've received an email like this, and I wanted to point out a few things before people get caught by this rather clever phishing attempt:
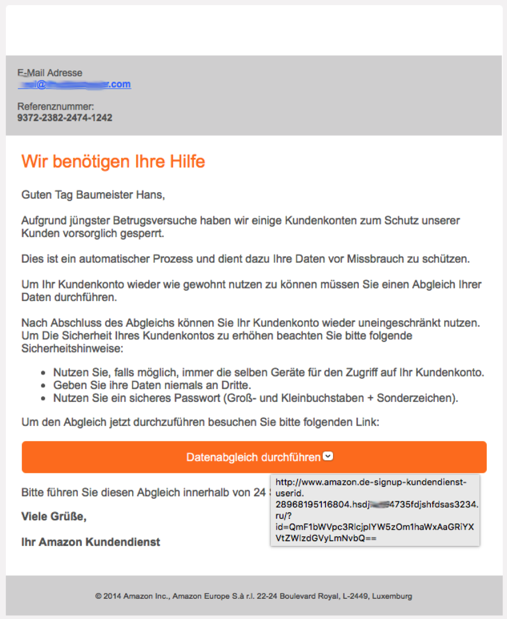
As you can see, this email contains no linked images, which is completely unusual for Amazon but probably done to avoid being classified as Spam.
The URL that pops up when you hover over the button also looks legit at first… it is an email in German and it seems to point to a German amazon URL.
But of course it doesn't. What gives it away, of course, is the fact that there is a hyphen after the "www.amazon.de" with some further "legitimizing" text, after that comes some more mumbo-jumbo that has nothing to do with a server. When we look at line 4 of the URL, we see "ru/?". on the line above, right before the "ru" is a period. That is the country part of the URL. If we go back a bit to the previous period, that is the actual server name. Here: "hsdj…4735fdjshfdsas3234". Forgive me for smudging out a bit - that is to prevent anyone from keying in the URL to see what happens and my email being registered as "alive".
Everything before the server name is irrelevant information that is likely thrown away by the recipient http server process. What is relevant is the "/?id=…" bit, which identifies my email address in their database.
What tipped me off, too, is that I don't have an amazon.de account with the email address this was sent to.
However, I'm sure plenty of people will "bite" onto this phishing attempt.
Even with more legit looking emails, it always pays to look at the URL that clicking on something will activate just to make sure it doesn't go to some Russian server…!
—
Update: Amazon.de replied to my tweet about this topic and sent this link to further information on how to identify legitimate Amazon emails.

As you can see, this email contains no linked images, which is completely unusual for Amazon but probably done to avoid being classified as Spam.
The URL that pops up when you hover over the button also looks legit at first… it is an email in German and it seems to point to a German amazon URL.
But of course it doesn't. What gives it away, of course, is the fact that there is a hyphen after the "www.amazon.de" with some further "legitimizing" text, after that comes some more mumbo-jumbo that has nothing to do with a server. When we look at line 4 of the URL, we see "ru/?". on the line above, right before the "ru" is a period. That is the country part of the URL. If we go back a bit to the previous period, that is the actual server name. Here: "hsdj…4735fdjshfdsas3234". Forgive me for smudging out a bit - that is to prevent anyone from keying in the URL to see what happens and my email being registered as "alive".
Everything before the server name is irrelevant information that is likely thrown away by the recipient http server process. What is relevant is the "/?id=…" bit, which identifies my email address in their database.
What tipped me off, too, is that I don't have an amazon.de account with the email address this was sent to.
However, I'm sure plenty of people will "bite" onto this phishing attempt.
Even with more legit looking emails, it always pays to look at the URL that clicking on something will activate just to make sure it doesn't go to some Russian server…!
—
Update: Amazon.de replied to my tweet about this topic and sent this link to further information on how to identify legitimate Amazon emails.
Comments
Phishing in the name of Apple
12.09.14
I never thought it would happen - but it happened: a Phishing email “got” me.
I was reading emails on my iPad when I found the following message:
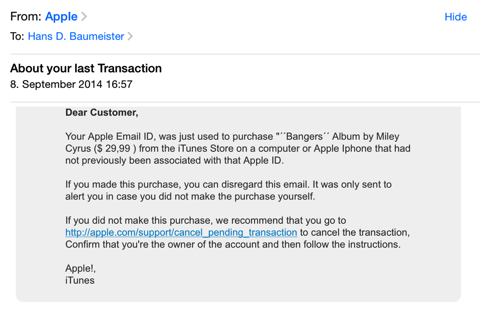
And you know what? They got me! I was sitting in the living room with a couple other people, talking about this and that and checking my emails while doing it. Failing grade for social competence there, and yes, I should have separated reading emails and talking into two separate actions... but - lets face it - the situation isn’t anything unusual, probably worldwide.
If I’d been concentrating on just one thing at a time, I would have noticed the odd structuring of text, I would have realized that it just plain isn’t possible to buy an album using my account on a device that isn’t registered, etc. etc. etc.
But I didn’t.
I panicked and clicked on the link. Here is what the real link - behind the fake one - points to:
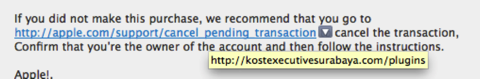
Mind you, the screenshot above is done on my Mac... you can just hover the mouse over the suppled URL in an Email message and up pops the real URL that is hidden behind it. You can’t do that on an iPad! Why? Beats me!
It is beyond me that modern email clients (and I put all of them in the same bag, folks) don’t do a comparison check on included URL’s before showing a message. The only way to hide a bad URL behind a seemingly good one is to encode the entire email in HTML; checking for inconsistencies isn’t difficult.
Especially on an iPad, just flagging an email with mismatched URL’s would be helpful - in fact, I see this as an absolute MUST-HAVE function (Apple, are you listening?).
What is “kostexecutivesurabaya.com”? It is a Malay website that states “If you have any business purpose, visiting relatives, holiday or have important business in the area of Surabaya and require Kost / temporary shelter, KostExecutiveSurabaya.com is the solution.” (thanks, Google Translate!).
The URL is registered to a company called “mediatechindonesia” in Jawa Timur, Indonesia. Wether it’s been hacked or not is tough to tell; I’m not going to waste my time getting in contact with the admin-c.
Interesting is the modus operandi. Instead of adding a unique key to the hidden URL (which would associate with my email-address, giving the phisher a heads-up on its status), it leads to a form page made up to look just like one from Apple. The issue has been registered, apparently, because any attempt to call up the URL again leads to a forgery warning:
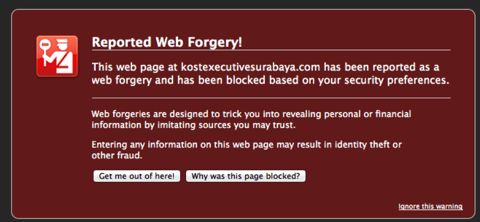
When I hit “ignore”, I get to an empty directory, so whatever the issue with the server was, it’s been taken care of.
Unfortunately, I didn’t take screenshots of the pages that were up, because they were shockingly well done - likely original HTML code from Apple’s website copied and used to make the Phish as believable as possible.
The first page asked you to enter your Apple credentials (Apple ID and password). This was followed by a form asking you to validate your payment information. This is where the fog in my brain was finally dispersed.
I immediately went to change my password for my Apple ID... you have to be VERY quick with this - if the Phisher is quicker, then you’ve lost your Apple ID to them. By the time you get it blocked, they’ve purchased all the musik, books and videos they need to entertain themselves for the next three years straight.
And here, I have to loudly criticize Apple: put yourself in my situation - you’re panicked. Your frantically trying to change your password. Go ahead, do the test. Put yourself in frantic mode, log onto the iTunes store and try to figure out how to change your password. Quick! Hurry! Too late...
Honestly, with the recent issues Apple had with iCloud - wether they are Apple problems or not - I would think security topics such as easy access to password changes or even to setting up two-factor authentication would be at the forefront of Apple management’s todo list.
Instead, even though I claim not to be an IT noob, I was unable to activate two-factor authentication without searching the web for instructions! And get this - you go to turn it on and... you have to wait three days! WTF, Apple? If I’m able to activate anything in my account, I already HAVE THE APPLE ID AND PASSWORD. Duh!!! Do you really think a three-day waiting period is going to make things more secure? I feel like I’ve applied for a divorce and the government is forcing me to think about my decision before concurring!
Steve, you went from us way too early!
I was reading emails on my iPad when I found the following message:

And you know what? They got me! I was sitting in the living room with a couple other people, talking about this and that and checking my emails while doing it. Failing grade for social competence there, and yes, I should have separated reading emails and talking into two separate actions... but - lets face it - the situation isn’t anything unusual, probably worldwide.
If I’d been concentrating on just one thing at a time, I would have noticed the odd structuring of text, I would have realized that it just plain isn’t possible to buy an album using my account on a device that isn’t registered, etc. etc. etc.
But I didn’t.
I panicked and clicked on the link. Here is what the real link - behind the fake one - points to:

Mind you, the screenshot above is done on my Mac... you can just hover the mouse over the suppled URL in an Email message and up pops the real URL that is hidden behind it. You can’t do that on an iPad! Why? Beats me!
It is beyond me that modern email clients (and I put all of them in the same bag, folks) don’t do a comparison check on included URL’s before showing a message. The only way to hide a bad URL behind a seemingly good one is to encode the entire email in HTML; checking for inconsistencies isn’t difficult.
Especially on an iPad, just flagging an email with mismatched URL’s would be helpful - in fact, I see this as an absolute MUST-HAVE function (Apple, are you listening?).
What is “kostexecutivesurabaya.com”? It is a Malay website that states “If you have any business purpose, visiting relatives, holiday or have important business in the area of Surabaya and require Kost / temporary shelter, KostExecutiveSurabaya.com is the solution.” (thanks, Google Translate!).
The URL is registered to a company called “mediatechindonesia” in Jawa Timur, Indonesia. Wether it’s been hacked or not is tough to tell; I’m not going to waste my time getting in contact with the admin-c.
Interesting is the modus operandi. Instead of adding a unique key to the hidden URL (which would associate with my email-address, giving the phisher a heads-up on its status), it leads to a form page made up to look just like one from Apple. The issue has been registered, apparently, because any attempt to call up the URL again leads to a forgery warning:

When I hit “ignore”, I get to an empty directory, so whatever the issue with the server was, it’s been taken care of.
Unfortunately, I didn’t take screenshots of the pages that were up, because they were shockingly well done - likely original HTML code from Apple’s website copied and used to make the Phish as believable as possible.
The first page asked you to enter your Apple credentials (Apple ID and password). This was followed by a form asking you to validate your payment information. This is where the fog in my brain was finally dispersed.
I immediately went to change my password for my Apple ID... you have to be VERY quick with this - if the Phisher is quicker, then you’ve lost your Apple ID to them. By the time you get it blocked, they’ve purchased all the musik, books and videos they need to entertain themselves for the next three years straight.
And here, I have to loudly criticize Apple: put yourself in my situation - you’re panicked. Your frantically trying to change your password. Go ahead, do the test. Put yourself in frantic mode, log onto the iTunes store and try to figure out how to change your password. Quick! Hurry! Too late...
Honestly, with the recent issues Apple had with iCloud - wether they are Apple problems or not - I would think security topics such as easy access to password changes or even to setting up two-factor authentication would be at the forefront of Apple management’s todo list.
Instead, even though I claim not to be an IT noob, I was unable to activate two-factor authentication without searching the web for instructions! And get this - you go to turn it on and... you have to wait three days! WTF, Apple? If I’m able to activate anything in my account, I already HAVE THE APPLE ID AND PASSWORD. Duh!!! Do you really think a three-day waiting period is going to make things more secure? I feel like I’ve applied for a divorce and the government is forcing me to think about my decision before concurring!
Steve, you went from us way too early!
Review of LastPass
27.06.14
If you’re looking for password management, please read my review of LastPass, which I can recommend without restrictions.
I’d been using the same - albeit complex - password for nearly all the internet (and intranet) sites I use... with more and more news about cracked servers coming in on a daily basis, I finally decided to do something about the situation.
I researched several sites that reviewed password managers and finally ended up with LastPass, as it fulfills several requirements I have:
LastPass ended up covering all of these requirements with bravado. It will auto-fill most webpages you call up automatically; some, it struggles with (strangely enough: my m0n0wall firewall in my local LAN is a candidate), but this is rarely the case.
Also quite nice is the recent addition of autofill on mobile devices, which makes working with passwords a snap for most apps / websites.
When I first signed up (the service costs $12/year, apps are free for all platforms), the safest method for multi-level authentication was a grid (unique to each user) you printed out. To authenticate, LastPass would give you five letter/number combinations which - when followed up on the grid - would generate five alphanumeric characters as an authentication code.
Recently, they have moved to using Google Authenticator, which reminds me of the RSA SecurID Token used to sign into VPNs. It works like a charm.
To further increase security, you can severely restrict the locale of the IP addresses that can be used to log in. I.e. if you know you’re never going to be in China, you can just close down all Chinese IP addresses as log-in sources. Sure, a Chinese hacker can VPN to an IP address based in Germany, for example, but the mechanism helps.
As the name implies, you do have to give your LastPass account one “last” password that you can easily remember but qualifies for a “safe” password. I.e.: don’t use your cat’s name here, because if someone figures it out, they have access to all of your passwords!
On first installation, LastPass offers to import all passwords from your browser(s). Since I used the browser auto-entry feature extensively, I let LastPass do this. After the fact, I’m not sure if this is a sensible step if you’re using the same password over and over, because you really don’t have much added value. On the other hand, you get a huge list of entries, some of which had up to 10 duplicates in my case, because browsers just don’t do the database thing very well.
LastPass will generate passwords for you; in fact, if you sign up to some service on the internet, LastPass consistently adds a small icon to the right of the fields where you are to enter and confirm the password to be used. I find this quite fascinating, since these fields have all sorts of different labels, etc., but perhaps there is a standard marking used in HTML to designate an entry field for the password.
In any case, if you click on this icon, LastPass will pop up a small window where you can not only generate a random password, but also change the parameters to be used, such as length, wether to make the password pronounceable or wether it can use special characters or not.
Especially the length and special characters settings can be quite important, as there are still services out there that restrict you to, say, 8 letters and/or numbers.
Once you have generated a password for the new service, LastPass offers to save the site (which is something you obviously want to do). You can name the site as you like and also select it as a favorite (which will make it come up at the top of the list in the LastPass panel), as well as assigning a category (such as “Online Shopping”). The categories can be typed in (for new ones) or selected from a dropdown list. They are optional, but very handy.
Perhaps odd at first is the fact that there is no LastPass App for Windows or Mac - you use it from a browser (all relevant browsers are supported). The mobile operating systems do have Apps to make the use simpler on these devices. On the mobile app, you can search for a site, for example (by any of its metadata) and chose “copy password do clipboard” if you need to manually paste it into a service. While you can search for sites in the browser-based “App”, to copy a password you have to open the entry, reveal the password and copy it to the clipboard manually - a bit cumbersome, but you get used to it.
The experience with Apple Safari on the Mac wasn’t so good, but because this is true not just for LastPass, I’ve switched to Firefox a couple of weeks ago. In Firefox, I sometimes have an issue where the Vault (as the database is called in LastPass) doesn’t come up when I click on the LastPass icon in the browser’s menu bar. Restarting Firefox fixes this; I’m not sure if it is a Firefox or a LastPass issue. As I don’t use Chrome much, I can’t say anything about stability, other than it works fine when I test it.
In order to get all your passwords to sync to all your devices (which is absolutely fabulous!), you will need a LastPass account. This also means that your passwords are synced to the LastPass server farm (albeit encrypted). Wether or not this is an issue for you is your decision; I think two concepts are relevant to make it:
1. Nothing on the internet is safe. If you want safe, go back to writing letters on paper and posting them. Oh, and hope no one opens the envelope that isn’t supposed to read the content...
2. I’m quite sure that lastpass.com is one of THE target sites for hackers. Imagine getting your hands on a couple of thousand user records... up to date and as far as I know, no breach has been reported...
You can use LastPass as a local-only installation - in which case your data never leaves your PC (or Mac). This version is also completely free-of-charge! So there is no reason not to test the software. If you only use a single PC or Mac, then this is all you need.
Check LastPass out here.
I’d been using the same - albeit complex - password for nearly all the internet (and intranet) sites I use... with more and more news about cracked servers coming in on a daily basis, I finally decided to do something about the situation.
I researched several sites that reviewed password managers and finally ended up with LastPass, as it fulfills several requirements I have:
- usability on Mac at least on par with Windows
- usable on iOS
- usable on Android
- auto-fill capability
- multi-level authentication for security
LastPass ended up covering all of these requirements with bravado. It will auto-fill most webpages you call up automatically; some, it struggles with (strangely enough: my m0n0wall firewall in my local LAN is a candidate), but this is rarely the case.
Also quite nice is the recent addition of autofill on mobile devices, which makes working with passwords a snap for most apps / websites.
When I first signed up (the service costs $12/year, apps are free for all platforms), the safest method for multi-level authentication was a grid (unique to each user) you printed out. To authenticate, LastPass would give you five letter/number combinations which - when followed up on the grid - would generate five alphanumeric characters as an authentication code.
Recently, they have moved to using Google Authenticator, which reminds me of the RSA SecurID Token used to sign into VPNs. It works like a charm.
To further increase security, you can severely restrict the locale of the IP addresses that can be used to log in. I.e. if you know you’re never going to be in China, you can just close down all Chinese IP addresses as log-in sources. Sure, a Chinese hacker can VPN to an IP address based in Germany, for example, but the mechanism helps.
As the name implies, you do have to give your LastPass account one “last” password that you can easily remember but qualifies for a “safe” password. I.e.: don’t use your cat’s name here, because if someone figures it out, they have access to all of your passwords!
On first installation, LastPass offers to import all passwords from your browser(s). Since I used the browser auto-entry feature extensively, I let LastPass do this. After the fact, I’m not sure if this is a sensible step if you’re using the same password over and over, because you really don’t have much added value. On the other hand, you get a huge list of entries, some of which had up to 10 duplicates in my case, because browsers just don’t do the database thing very well.
LastPass will generate passwords for you; in fact, if you sign up to some service on the internet, LastPass consistently adds a small icon to the right of the fields where you are to enter and confirm the password to be used. I find this quite fascinating, since these fields have all sorts of different labels, etc., but perhaps there is a standard marking used in HTML to designate an entry field for the password.
In any case, if you click on this icon, LastPass will pop up a small window where you can not only generate a random password, but also change the parameters to be used, such as length, wether to make the password pronounceable or wether it can use special characters or not.
Especially the length and special characters settings can be quite important, as there are still services out there that restrict you to, say, 8 letters and/or numbers.
Once you have generated a password for the new service, LastPass offers to save the site (which is something you obviously want to do). You can name the site as you like and also select it as a favorite (which will make it come up at the top of the list in the LastPass panel), as well as assigning a category (such as “Online Shopping”). The categories can be typed in (for new ones) or selected from a dropdown list. They are optional, but very handy.
Perhaps odd at first is the fact that there is no LastPass App for Windows or Mac - you use it from a browser (all relevant browsers are supported). The mobile operating systems do have Apps to make the use simpler on these devices. On the mobile app, you can search for a site, for example (by any of its metadata) and chose “copy password do clipboard” if you need to manually paste it into a service. While you can search for sites in the browser-based “App”, to copy a password you have to open the entry, reveal the password and copy it to the clipboard manually - a bit cumbersome, but you get used to it.
The experience with Apple Safari on the Mac wasn’t so good, but because this is true not just for LastPass, I’ve switched to Firefox a couple of weeks ago. In Firefox, I sometimes have an issue where the Vault (as the database is called in LastPass) doesn’t come up when I click on the LastPass icon in the browser’s menu bar. Restarting Firefox fixes this; I’m not sure if it is a Firefox or a LastPass issue. As I don’t use Chrome much, I can’t say anything about stability, other than it works fine when I test it.
In order to get all your passwords to sync to all your devices (which is absolutely fabulous!), you will need a LastPass account. This also means that your passwords are synced to the LastPass server farm (albeit encrypted). Wether or not this is an issue for you is your decision; I think two concepts are relevant to make it:
1. Nothing on the internet is safe. If you want safe, go back to writing letters on paper and posting them. Oh, and hope no one opens the envelope that isn’t supposed to read the content...
2. I’m quite sure that lastpass.com is one of THE target sites for hackers. Imagine getting your hands on a couple of thousand user records... up to date and as far as I know, no breach has been reported...
You can use LastPass as a local-only installation - in which case your data never leaves your PC (or Mac). This version is also completely free-of-charge! So there is no reason not to test the software. If you only use a single PC or Mac, then this is all you need.
Check LastPass out here.
Beware of Facebook Phishing
18.05.14
All,
a quick word of warning, as there is a new batch of Facebook-lookalike phishing mails being sent out:
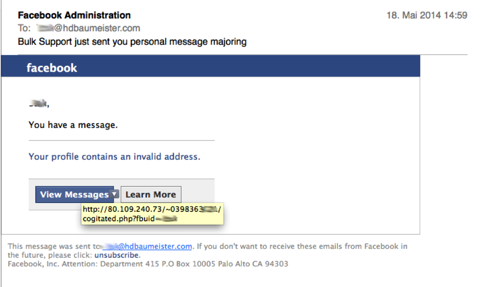
This is an attempt to - at the very least - verify your email address (in this case, it wasn’t the email address I use for my facebook account), possibly with additional attempts to gain details about your. I didn’t click on the button, so I couldn’t tell you what popped up... ;-)
Oddly enough, the sender didn’t try to mask the sending address; it came from directix@info.gamanetwork.com. Or perhaps it _was_ masked, though in that case I would have expected a service@facebook.com or similar...
Whenever you get an email with buttons like these - even if it really REALLY looks like it is from a legitimate source, always - ALWAYS - hover with your mouse over the button. Your mail software should show you the URL that button will call when clicked (if not, time to switch to something proper).
a quick word of warning, as there is a new batch of Facebook-lookalike phishing mails being sent out:

This is an attempt to - at the very least - verify your email address (in this case, it wasn’t the email address I use for my facebook account), possibly with additional attempts to gain details about your. I didn’t click on the button, so I couldn’t tell you what popped up... ;-)
Oddly enough, the sender didn’t try to mask the sending address; it came from directix@info.gamanetwork.com. Or perhaps it _was_ masked, though in that case I would have expected a service@facebook.com or similar...
Whenever you get an email with buttons like these - even if it really REALLY looks like it is from a legitimate source, always - ALWAYS - hover with your mouse over the button. Your mail software should show you the URL that button will call when clicked (if not, time to switch to something proper).
FreeNAS Part 1 - bootable USB Stick
24.02.14
As time goes on, storage needs grow.
My RAID-1 IcyBox with 3GB was filling up fast, with less than half a TB left. NAS storage was maxed out (okay, its an older Synology 207+ with 2x 1TB, so nothing to brag about). Something bigger needed to be put together.
As I’m also using a single-drive Synology NAS (DS110J) for Email storage, SMTP and Surveillance Station, I know what Synology’s current NAS OS 4.3 can do (and can’t) - really, it is quite good, even though it has some issues with Jave and uses Flash (of all things) in its GUI.
Needless to say, I find the cost of a four-drive Synology NAS (or any other reputable manufacturer, for that matter) almost prohibitive, considering what you’re getting. By chance, I happened across several blog posts describing FreeNAS being implemented on an HP ProLiant Microserver. Surprisingly, you can get the current model (N54L) of that server for under 200€ on Amazon!
Since I’d done tests with FreeNAS, OpenMediaVault and NAS4Free in respective VM’s, I’d come to the conclusion that FreeNAS would be the way to go for my needs. It is based on FreeBSD and offers extremely simple boot from a USB stick image.
In this first part of a series of blog entries on FreeNAS, I’ll detail my first experiences with getting the software to boot from a USB stick.
1. Installation on bootable USB stick
Getting that image onto a stick and getting it to boot proved to be trickier than I expected. Reading several posts on the subject, the procedure that ended up working was as follows:
1) Extract run-time image from installation package
Download the IMG file for the installation package from here (make sure you choose the “Current Stable Release” on the right side).
There is an IMG inside the IMG used for a stick-based (or CD-based) installation that is the actual run-time image of FreeNAS. I.e.: open the IMG used for installation (which on a Mac is very easy) and copy the file FreeNAS-x64.img.xz to someplace where you’ll find it easily (i.e. the Desktop). The XZ format is a compression type used, for example, by
Then, pop the USB stick you want to install on (at least 2GB in size) into a port and open Terminal. First, you need to find out which disk device connects to the USB stick:
diskutil list
this should list the USB stick in a format similar to this (this is from my system, your device will be different).
/dev/disk3
#: TYPE NAME SIZE IDENTIFIER
0: Untitled *4.1 GB disk3
Next, you’ll want to unmount the stick (don’t eject it!) using the Terminal so that it becomes overwriteable:
diskutil unmountDisk /dev/disk3
Again, your device name may be different.
Lastly, you’ll write the runtime image onto the stick using the dd command:
sudo dd if=path_to_img of=/dev/disk3 bs=64k
Getting the path to the IMG file right is really simple on the Mac: just type in “sudo dd if=“ and then drag and drop the IMG file onto the Terminal window; Terminal will enter the path correctly. The bs qualifier indicates the blocksize to use for the copy. You’ll have to enter the password of an administrator account to run the command.
Copying everything over will take quite awhile; we’re talking over 220 MB after all (and the usual slowness of a USB stick in writing), so don’t be discouraged if, after an hour, the command still hasn’t finished.
Now you can pull the USB stick and pop it into the ProLiant’s internal USB port (on the N54L it is at the bottom left when you open the drive bay door).
My RAID-1 IcyBox with 3GB was filling up fast, with less than half a TB left. NAS storage was maxed out (okay, its an older Synology 207+ with 2x 1TB, so nothing to brag about). Something bigger needed to be put together.
As I’m also using a single-drive Synology NAS (DS110J) for Email storage, SMTP and Surveillance Station, I know what Synology’s current NAS OS 4.3 can do (and can’t) - really, it is quite good, even though it has some issues with Jave and uses Flash (of all things) in its GUI.
Needless to say, I find the cost of a four-drive Synology NAS (or any other reputable manufacturer, for that matter) almost prohibitive, considering what you’re getting. By chance, I happened across several blog posts describing FreeNAS being implemented on an HP ProLiant Microserver. Surprisingly, you can get the current model (N54L) of that server for under 200€ on Amazon!
Since I’d done tests with FreeNAS, OpenMediaVault and NAS4Free in respective VM’s, I’d come to the conclusion that FreeNAS would be the way to go for my needs. It is based on FreeBSD and offers extremely simple boot from a USB stick image.
In this first part of a series of blog entries on FreeNAS, I’ll detail my first experiences with getting the software to boot from a USB stick.
1. Installation on bootable USB stick
Getting that image onto a stick and getting it to boot proved to be trickier than I expected. Reading several posts on the subject, the procedure that ended up working was as follows:
1) Extract run-time image from installation package
Download the IMG file for the installation package from here (make sure you choose the “Current Stable Release” on the right side).
There is an IMG inside the IMG used for a stick-based (or CD-based) installation that is the actual run-time image of FreeNAS. I.e.: open the IMG used for installation (which on a Mac is very easy) and copy the file FreeNAS-x64.img.xz to someplace where you’ll find it easily (i.e. the Desktop). The XZ format is a compression type used, for example, by
Then, pop the USB stick you want to install on (at least 2GB in size) into a port and open Terminal. First, you need to find out which disk device connects to the USB stick:
diskutil list
this should list the USB stick in a format similar to this (this is from my system, your device will be different).
/dev/disk3
#: TYPE NAME SIZE IDENTIFIER
0: Untitled *4.1 GB disk3
Next, you’ll want to unmount the stick (don’t eject it!) using the Terminal so that it becomes overwriteable:
diskutil unmountDisk /dev/disk3
Again, your device name may be different.
Lastly, you’ll write the runtime image onto the stick using the dd command:
sudo dd if=path_to_img of=/dev/disk3 bs=64k
Getting the path to the IMG file right is really simple on the Mac: just type in “sudo dd if=“ and then drag and drop the IMG file onto the Terminal window; Terminal will enter the path correctly. The bs qualifier indicates the blocksize to use for the copy. You’ll have to enter the password of an administrator account to run the command.
Copying everything over will take quite awhile; we’re talking over 220 MB after all (and the usual slowness of a USB stick in writing), so don’t be discouraged if, after an hour, the command still hasn’t finished.
Now you can pull the USB stick and pop it into the ProLiant’s internal USB port (on the N54L it is at the bottom left when you open the drive bay door).
Internet Appliance Botnet-Attack
21.01.14
This article by Proofpoint seems to indicate that everyday, connected appliances such as TV’s, Media Centers, Network Routers and even a Refrigerator have been “assimilated” into a Botnet to send out Spam Emails.
While a Media Center likely has a full-blown Linux (or Windows, in the case of Microsoft devices) on it, a Router certainly will not. I’ve used a number of different Internet routers in the last 15 years, such as a simple D-Link device, an AVM Fritzbox and, in the last couple of years an appliance with m0n0wall installed.
I can’t, for the life of me, imagine that these offer the ability to install a botnet. Sure, give an experienced hacker a device that is open to the WAN side (none are when you pull them out of the box!) and enough time, they will likely gain access to at least the admin menu. Using that, I would imagine it is possible to install a different, roll-your-own firmware that would render the device into a “Borg”. This would, in all likelyhood render the router incapable of doing “it’s thing”, which would obviously uncover the heist very quickly.
That said, botnets aren’t installed by a human taking an hour to hack into the device and load a new firmware (or install malware), but by automated mechanisms run - usually - on other “assimilated” bots.
TV’s and refrigerators will likely also have slimmed-down Linux OS’s that would probably require replacing at least the Kernel to function as a bot; in the case of a TV, that should make using the device spotty at best.
Also, don’t forget: generally, these devices are all in a private network of some sort, protected by IP filters. Again, hackable by a human (given enough time) for sure, but likely not by an automaton.
I’m not a botnet expert, but this sounds too outlandish to be more than a highly interpreted piece of marketing...
While a Media Center likely has a full-blown Linux (or Windows, in the case of Microsoft devices) on it, a Router certainly will not. I’ve used a number of different Internet routers in the last 15 years, such as a simple D-Link device, an AVM Fritzbox and, in the last couple of years an appliance with m0n0wall installed.
I can’t, for the life of me, imagine that these offer the ability to install a botnet. Sure, give an experienced hacker a device that is open to the WAN side (none are when you pull them out of the box!) and enough time, they will likely gain access to at least the admin menu. Using that, I would imagine it is possible to install a different, roll-your-own firmware that would render the device into a “Borg”. This would, in all likelyhood render the router incapable of doing “it’s thing”, which would obviously uncover the heist very quickly.
That said, botnets aren’t installed by a human taking an hour to hack into the device and load a new firmware (or install malware), but by automated mechanisms run - usually - on other “assimilated” bots.
TV’s and refrigerators will likely also have slimmed-down Linux OS’s that would probably require replacing at least the Kernel to function as a bot; in the case of a TV, that should make using the device spotty at best.
Also, don’t forget: generally, these devices are all in a private network of some sort, protected by IP filters. Again, hackable by a human (given enough time) for sure, but likely not by an automaton.
I’m not a botnet expert, but this sounds too outlandish to be more than a highly interpreted piece of marketing...
Phishing wird "intelligenter"
15.01.14
Die Zeiten von “I am the brother of the president of Nigeria” sind zwar nicht vorbei, dafür werden die Phishing-Betreiber “intelligenter” was die Aufmachung ihrer Emails angeht.
Heute ist diese Email bei mir angekommen:
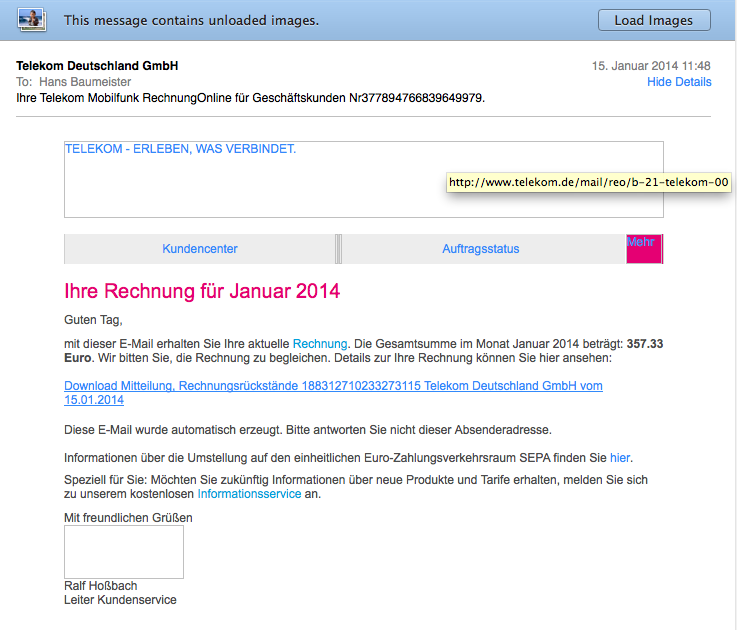
Ich habe explizit die Bilder nicht geladen, da in Bildaufrufen oft eine Kodierung versteckt wird, die Rückschlüsse wie eine Empfangsbestätigung ermöglicht. Zum anderen aber, um aufzeigen zu können, dass die Bilder tatsächlich von telekom.de gezogen werden (die gelb hinterlegte Anzeige kommt beim Mouse-Hover über dem Bild und gibt die Quell-URL an).
Lediglich der Link für den Download zeigt nicht auf die Telekom, sondern auf die URL http://581khg.nuusi.net/telekom/ (bitte nicht testen!!!).
Wäre ich Telekom-Kunde, hätte ich ggf. ungeprüft draufgeklickt. Um so wichtiger ist die Funktion, die jeder moderne Mailclient bietet: via Mouse-Hover sich ein Bild von der URL zu machen, die tatsächlich beim Anklicken aufgerufen wird. Oft werden nämlich http: URLs angegeben, hinter denen sich ganz andere URL’s verbergen.
Heute ist diese Email bei mir angekommen:

Ich habe explizit die Bilder nicht geladen, da in Bildaufrufen oft eine Kodierung versteckt wird, die Rückschlüsse wie eine Empfangsbestätigung ermöglicht. Zum anderen aber, um aufzeigen zu können, dass die Bilder tatsächlich von telekom.de gezogen werden (die gelb hinterlegte Anzeige kommt beim Mouse-Hover über dem Bild und gibt die Quell-URL an).
Lediglich der Link für den Download zeigt nicht auf die Telekom, sondern auf die URL http://581khg.nuusi.net/telekom/ (bitte nicht testen!!!).
Wäre ich Telekom-Kunde, hätte ich ggf. ungeprüft draufgeklickt. Um so wichtiger ist die Funktion, die jeder moderne Mailclient bietet: via Mouse-Hover sich ein Bild von der URL zu machen, die tatsächlich beim Anklicken aufgerufen wird. Oft werden nämlich http: URLs angegeben, hinter denen sich ganz andere URL’s verbergen.
Check your router!
13.01.14
I was pretty surprised to read in this article, that a number of brand-name routers offer a “backdoor” via their WAN IP, Port 32764. Via this port, it is possible to read out various variables and settings, the knowledge of which greatly aid a hacker trying to get into the private network behind the device.
In some cases, it was apparently possible to change settings in the router via this port!!!
So: you may do well to make sure your router isn’t affected. Heise Verlag of Germany offers a free scan service that - using your IP address (which your Webbrowser knows about) - scans your router from the outside to see if it can find any open ports (that shouldn’t be).
For all you non-German-speakers out there, just click the “Ich bestätige, dass ich berechtigt bin, die IP-Adresse x.x.x.x zu scannen.” Checkbox (which indicates that you’re permitting the port scan to happen, and that you have the right to have that address scanned) and select the “Router-Backdoor” radio button. Then hit “Scan starten” and you get a result nearly instantly.
You may also wish to run the “Router” version of the test, which checks more ports as well as the just discussed “backdoor” port:
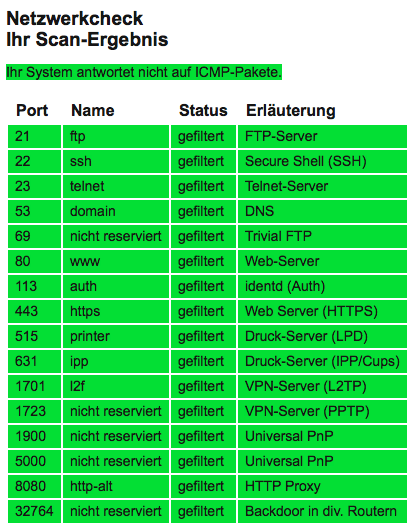
If the result is green, you’re good to go - if it is red, well then you have a problem.
If you’re versed in IP ports, you may also want to do the check with either the “Windows standard” or “UNIX standard” radio buttons selected - these do extensive port scans based on wether you’re using a Windows or a UNIX-based (MacOS, Linux, etc.) computer.
In some cases, it was apparently possible to change settings in the router via this port!!!
So: you may do well to make sure your router isn’t affected. Heise Verlag of Germany offers a free scan service that - using your IP address (which your Webbrowser knows about) - scans your router from the outside to see if it can find any open ports (that shouldn’t be).
For all you non-German-speakers out there, just click the “Ich bestätige, dass ich berechtigt bin, die IP-Adresse x.x.x.x zu scannen.” Checkbox (which indicates that you’re permitting the port scan to happen, and that you have the right to have that address scanned) and select the “Router-Backdoor” radio button. Then hit “Scan starten” and you get a result nearly instantly.
You may also wish to run the “Router” version of the test, which checks more ports as well as the just discussed “backdoor” port:

If the result is green, you’re good to go - if it is red, well then you have a problem.
If you’re versed in IP ports, you may also want to do the check with either the “Windows standard” or “UNIX standard” radio buttons selected - these do extensive port scans based on wether you’re using a Windows or a UNIX-based (MacOS, Linux, etc.) computer.
Java issues with Surveillance Station 6 resolved
27.06.13
I’ve been using several Synology DS NAS devices for a number of years quite successfully. One of the really excellent features is Surveillance Station, a software that lets you configure an IP camera and have the NAS record video from it when there is movement within the picture.
I won’t go into details on the solution (that is covered quite well on the Synology website) but rather touch on an issue that has come up with the latest update of version 6. This, as it turned out, had some really serious issues with a Java update 1.7.x from Apple, resulting in the software not being able to display recorded video on a current and updated Mac (Mountain Lion).
There is lots of chatter on this topic in various forums, including the one on the Synology site.
Finally, Synology has published a fix for the issue, which requires a bit of admin-level work in a Terminal.
In case that link should go away for some reason, here are the steps required to resolve the issue (it helped me - everything works like a charm once again):
1. On your Mac, go to Applications > Utilities and then open Terminal. Enter the following command, and press the Return or Enter key:
sudo mkdir -p /Library/Internet\ Plug-Ins/disabled
2. Enter the following command, and press the Return or Enter key:
sudo mv /Library/Internet\ Plug-Ins/JavaAppletPlugin.plugin /Library/Internet\ Plug-Ins/disabled
3. Enter the following command, and press the Return or Enter key:
sudo ln -sf /System/Library/Java/Support/Deploy.bundle/Contents/Resources/JavaPlugin2_NPAPI.plugin /Library/Internet\ Plug-Ins/JavaAppletPlugin.plugin
4. Enter the following command, and press the Return or Enter key:
sudo /usr/libexec/PlistBuddy -c "Delete :JavaWebComponentVersionMinimum" /System/Library/CoreServices/CoreTypes.bundle/Contents/Resources/XProtect.meta.plist
Please note that you’ll have to have admin priviledges or log into an admin account when sudo asks you to.
I won’t go into details on the solution (that is covered quite well on the Synology website) but rather touch on an issue that has come up with the latest update of version 6. This, as it turned out, had some really serious issues with a Java update 1.7.x from Apple, resulting in the software not being able to display recorded video on a current and updated Mac (Mountain Lion).
There is lots of chatter on this topic in various forums, including the one on the Synology site.
Finally, Synology has published a fix for the issue, which requires a bit of admin-level work in a Terminal.
In case that link should go away for some reason, here are the steps required to resolve the issue (it helped me - everything works like a charm once again):
1. On your Mac, go to Applications > Utilities and then open Terminal. Enter the following command, and press the Return or Enter key:
sudo mkdir -p /Library/Internet\ Plug-Ins/disabled
2. Enter the following command, and press the Return or Enter key:
sudo mv /Library/Internet\ Plug-Ins/JavaAppletPlugin.plugin /Library/Internet\ Plug-Ins/disabled
3. Enter the following command, and press the Return or Enter key:
sudo ln -sf /System/Library/Java/Support/Deploy.bundle/Contents/Resources/JavaPlugin2_NPAPI.plugin /Library/Internet\ Plug-Ins/JavaAppletPlugin.plugin
4. Enter the following command, and press the Return or Enter key:
sudo /usr/libexec/PlistBuddy -c "Delete :JavaWebComponentVersionMinimum" /System/Library/CoreServices/CoreTypes.bundle/Contents/Resources/XProtect.meta.plist
Please note that you’ll have to have admin priviledges or log into an admin account when sudo asks you to.
LinkedIn Phishing after Security Breach
15.11.12
Unbelievable: the newest phishing emails are LinkedIn-branded and convinced me to click on the link, even though I tend to be a very suspicious person in these things:
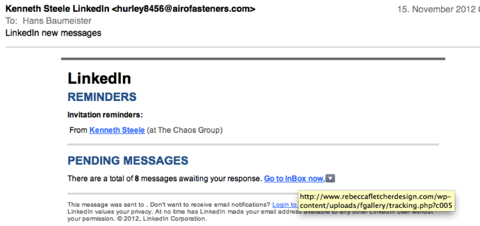
The screenshot above shows the URL that is linked to the blue text.
The URL redirects (after registering everything there is to register about your computer, surely) to Microsoft, strangely enough.
This most likely has to do with the recent security breach at LinkedIn, how else should anyone know the email address that I registered in my LinkedIn account?
http://www.rebeccafletcherdesign.com by the way seems a harmless enough URL - perhaps it was compromised as well?

The screenshot above shows the URL that is linked to the blue text.
The URL redirects (after registering everything there is to register about your computer, surely) to Microsoft, strangely enough.
This most likely has to do with the recent security breach at LinkedIn, how else should anyone know the email address that I registered in my LinkedIn account?
http://www.rebeccafletcherdesign.com by the way seems a harmless enough URL - perhaps it was compromised as well?
bit.ly hoax by Twitter App?
09.08.12
When I read interesting tweets on my iPad, I’ll send them to myself by email so that I can follow-up on the link at a later date.
I came across an article I wanted to comment (see here) and sent the tweet, as usual, by email. It came out okay, I clicked on the link in the email to open the URL (shortened on bit.ly) and: This is weird.
What opened was a t.co-shortened URL that led to an emtpy site (not, as you would expect, to a 404 error). Oddly enough, the tweet went to the right site (via the bit.ly URL) when I opened it up on my iPad!
Here is a region snap of my email message with the underlying URL, that is actually executed when clicking on the link, exposed:
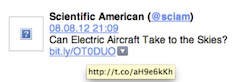
What generated this fake URL? It could only have been the Twitter App on my iPad… but why?
t.co is Twitter’s own URL shortner.
Veeeery mysterious!
I came across an article I wanted to comment (see here) and sent the tweet, as usual, by email. It came out okay, I clicked on the link in the email to open the URL (shortened on bit.ly) and: This is weird.
What opened was a t.co-shortened URL that led to an emtpy site (not, as you would expect, to a 404 error). Oddly enough, the tweet went to the right site (via the bit.ly URL) when I opened it up on my iPad!
Here is a region snap of my email message with the underlying URL, that is actually executed when clicking on the link, exposed:

What generated this fake URL? It could only have been the Twitter App on my iPad… but why?
t.co is Twitter’s own URL shortner.
Veeeery mysterious!
Passwords - a modern Tragedy
13.06.12
Since 1985, I’d been using a very simple, one-word password that I’d learned from a fellow student at RIT. I protected everything (and I mean everything!) digital with this password. To this day, it hasn’t been compromised.
After, amongst others, the password-debacle at LinkedIn, mixed with a growing number of services requiring high-complexitiy passwords, I’ve modified this original password with capital letters, symbols and digits. I can still remember it quite easily, but doing a split-second password entry on a keyboard has become a fond memory.
With shift keys to press and digits to hit properly, entering this new password has become quite a chore, especially on my iPhone with its dinky, made-for-babies on-screen keyboard. Why is it, by the way, that Apple hasn’t implemented a landscape-orientation keyboard for this?
In any case, with the number of electronic services that one uses on the increase, so is the number of separate entities requiring some form of secure identification. If the password doesn’t need changing regularly, then - with “remember me on this computer” features - this isn’t such an issue. Often, though, it is just plain annoying.
With different password complexity requirements, one password - even it if is complex enough to be very secure - won’t suffice for every service.
Why is it that we have highly integrated technologies like an iPhone, but no halfway simple mechanism to automate personal identification? The user-facing camera on my iPhone should, for example, suffice in resolution and quality for a biometric check of the face (okay, I admit it: I haven’t a clue as to how this is done, but my imagination tells me it should be doable).
Why hasn’t someone implemented a bluetooth device that I can carry and link to my laptop, smartphone, desktop to identify me securely, perhaps via a smartcard and 5-digit PIN?
After, amongst others, the password-debacle at LinkedIn, mixed with a growing number of services requiring high-complexitiy passwords, I’ve modified this original password with capital letters, symbols and digits. I can still remember it quite easily, but doing a split-second password entry on a keyboard has become a fond memory.
With shift keys to press and digits to hit properly, entering this new password has become quite a chore, especially on my iPhone with its dinky, made-for-babies on-screen keyboard. Why is it, by the way, that Apple hasn’t implemented a landscape-orientation keyboard for this?
In any case, with the number of electronic services that one uses on the increase, so is the number of separate entities requiring some form of secure identification. If the password doesn’t need changing regularly, then - with “remember me on this computer” features - this isn’t such an issue. Often, though, it is just plain annoying.
With different password complexity requirements, one password - even it if is complex enough to be very secure - won’t suffice for every service.
Why is it that we have highly integrated technologies like an iPhone, but no halfway simple mechanism to automate personal identification? The user-facing camera on my iPhone should, for example, suffice in resolution and quality for a biometric check of the face (okay, I admit it: I haven’t a clue as to how this is done, but my imagination tells me it should be doable).
Why hasn’t someone implemented a bluetooth device that I can carry and link to my laptop, smartphone, desktop to identify me securely, perhaps via a smartcard and 5-digit PIN?