Phishing
Phishing mails getting more clever
This is the second time I've received an email like this, and I wanted to point out a few things before people get caught by this rather clever phishing attempt:
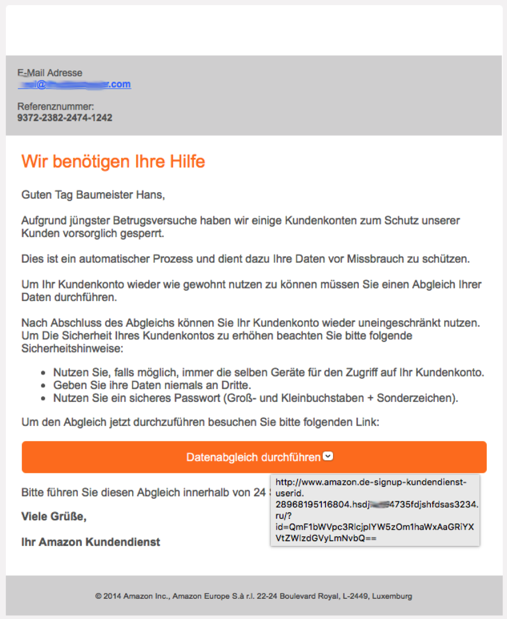
As you can see, this email contains no linked images, which is completely unusual for Amazon but probably done to avoid being classified as Spam.
The URL that pops up when you hover over the button also looks legit at first… it is an email in German and it seems to point to a German amazon URL.
But of course it doesn't. What gives it away, of course, is the fact that there is a hyphen after the "www.amazon.de" with some further "legitimizing" text, after that comes some more mumbo-jumbo that has nothing to do with a server. When we look at line 4 of the URL, we see "ru/?". on the line above, right before the "ru" is a period. That is the country part of the URL. If we go back a bit to the previous period, that is the actual server name. Here: "hsdj…4735fdjshfdsas3234". Forgive me for smudging out a bit - that is to prevent anyone from keying in the URL to see what happens and my email being registered as "alive".
Everything before the server name is irrelevant information that is likely thrown away by the recipient http server process. What is relevant is the "/?id=…" bit, which identifies my email address in their database.
What tipped me off, too, is that I don't have an amazon.de account with the email address this was sent to.
However, I'm sure plenty of people will "bite" onto this phishing attempt.
Even with more legit looking emails, it always pays to look at the URL that clicking on something will activate just to make sure it doesn't go to some Russian server…!
—
Update: Amazon.de replied to my tweet about this topic and sent this link to further information on how to identify legitimate Amazon emails.

As you can see, this email contains no linked images, which is completely unusual for Amazon but probably done to avoid being classified as Spam.
The URL that pops up when you hover over the button also looks legit at first… it is an email in German and it seems to point to a German amazon URL.
But of course it doesn't. What gives it away, of course, is the fact that there is a hyphen after the "www.amazon.de" with some further "legitimizing" text, after that comes some more mumbo-jumbo that has nothing to do with a server. When we look at line 4 of the URL, we see "ru/?". on the line above, right before the "ru" is a period. That is the country part of the URL. If we go back a bit to the previous period, that is the actual server name. Here: "hsdj…4735fdjshfdsas3234". Forgive me for smudging out a bit - that is to prevent anyone from keying in the URL to see what happens and my email being registered as "alive".
Everything before the server name is irrelevant information that is likely thrown away by the recipient http server process. What is relevant is the "/?id=…" bit, which identifies my email address in their database.
What tipped me off, too, is that I don't have an amazon.de account with the email address this was sent to.
However, I'm sure plenty of people will "bite" onto this phishing attempt.
Even with more legit looking emails, it always pays to look at the URL that clicking on something will activate just to make sure it doesn't go to some Russian server…!
—
Update: Amazon.de replied to my tweet about this topic and sent this link to further information on how to identify legitimate Amazon emails.
Comments
Phishing in the name of Apple
I never thought it would happen - but it happened: a Phishing email “got” me.
I was reading emails on my iPad when I found the following message:
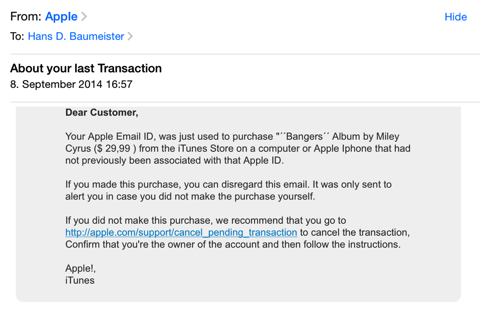
And you know what? They got me! I was sitting in the living room with a couple other people, talking about this and that and checking my emails while doing it. Failing grade for social competence there, and yes, I should have separated reading emails and talking into two separate actions... but - lets face it - the situation isn’t anything unusual, probably worldwide.
If I’d been concentrating on just one thing at a time, I would have noticed the odd structuring of text, I would have realized that it just plain isn’t possible to buy an album using my account on a device that isn’t registered, etc. etc. etc.
But I didn’t.
I panicked and clicked on the link. Here is what the real link - behind the fake one - points to:
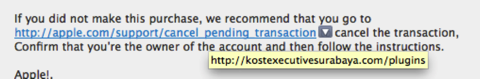
Mind you, the screenshot above is done on my Mac... you can just hover the mouse over the suppled URL in an Email message and up pops the real URL that is hidden behind it. You can’t do that on an iPad! Why? Beats me!
It is beyond me that modern email clients (and I put all of them in the same bag, folks) don’t do a comparison check on included URL’s before showing a message. The only way to hide a bad URL behind a seemingly good one is to encode the entire email in HTML; checking for inconsistencies isn’t difficult.
Especially on an iPad, just flagging an email with mismatched URL’s would be helpful - in fact, I see this as an absolute MUST-HAVE function (Apple, are you listening?).
What is “kostexecutivesurabaya.com”? It is a Malay website that states “If you have any business purpose, visiting relatives, holiday or have important business in the area of Surabaya and require Kost / temporary shelter, KostExecutiveSurabaya.com is the solution.” (thanks, Google Translate!).
The URL is registered to a company called “mediatechindonesia” in Jawa Timur, Indonesia. Wether it’s been hacked or not is tough to tell; I’m not going to waste my time getting in contact with the admin-c.
Interesting is the modus operandi. Instead of adding a unique key to the hidden URL (which would associate with my email-address, giving the phisher a heads-up on its status), it leads to a form page made up to look just like one from Apple. The issue has been registered, apparently, because any attempt to call up the URL again leads to a forgery warning:
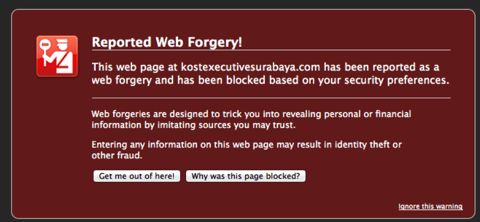
When I hit “ignore”, I get to an empty directory, so whatever the issue with the server was, it’s been taken care of.
Unfortunately, I didn’t take screenshots of the pages that were up, because they were shockingly well done - likely original HTML code from Apple’s website copied and used to make the Phish as believable as possible.
The first page asked you to enter your Apple credentials (Apple ID and password). This was followed by a form asking you to validate your payment information. This is where the fog in my brain was finally dispersed.
I immediately went to change my password for my Apple ID... you have to be VERY quick with this - if the Phisher is quicker, then you’ve lost your Apple ID to them. By the time you get it blocked, they’ve purchased all the musik, books and videos they need to entertain themselves for the next three years straight.
And here, I have to loudly criticize Apple: put yourself in my situation - you’re panicked. Your frantically trying to change your password. Go ahead, do the test. Put yourself in frantic mode, log onto the iTunes store and try to figure out how to change your password. Quick! Hurry! Too late...
Honestly, with the recent issues Apple had with iCloud - wether they are Apple problems or not - I would think security topics such as easy access to password changes or even to setting up two-factor authentication would be at the forefront of Apple management’s todo list.
Instead, even though I claim not to be an IT noob, I was unable to activate two-factor authentication without searching the web for instructions! And get this - you go to turn it on and... you have to wait three days! WTF, Apple? If I’m able to activate anything in my account, I already HAVE THE APPLE ID AND PASSWORD. Duh!!! Do you really think a three-day waiting period is going to make things more secure? I feel like I’ve applied for a divorce and the government is forcing me to think about my decision before concurring!
Steve, you went from us way too early!
I was reading emails on my iPad when I found the following message:

And you know what? They got me! I was sitting in the living room with a couple other people, talking about this and that and checking my emails while doing it. Failing grade for social competence there, and yes, I should have separated reading emails and talking into two separate actions... but - lets face it - the situation isn’t anything unusual, probably worldwide.
If I’d been concentrating on just one thing at a time, I would have noticed the odd structuring of text, I would have realized that it just plain isn’t possible to buy an album using my account on a device that isn’t registered, etc. etc. etc.
But I didn’t.
I panicked and clicked on the link. Here is what the real link - behind the fake one - points to:

Mind you, the screenshot above is done on my Mac... you can just hover the mouse over the suppled URL in an Email message and up pops the real URL that is hidden behind it. You can’t do that on an iPad! Why? Beats me!
It is beyond me that modern email clients (and I put all of them in the same bag, folks) don’t do a comparison check on included URL’s before showing a message. The only way to hide a bad URL behind a seemingly good one is to encode the entire email in HTML; checking for inconsistencies isn’t difficult.
Especially on an iPad, just flagging an email with mismatched URL’s would be helpful - in fact, I see this as an absolute MUST-HAVE function (Apple, are you listening?).
What is “kostexecutivesurabaya.com”? It is a Malay website that states “If you have any business purpose, visiting relatives, holiday or have important business in the area of Surabaya and require Kost / temporary shelter, KostExecutiveSurabaya.com is the solution.” (thanks, Google Translate!).
The URL is registered to a company called “mediatechindonesia” in Jawa Timur, Indonesia. Wether it’s been hacked or not is tough to tell; I’m not going to waste my time getting in contact with the admin-c.
Interesting is the modus operandi. Instead of adding a unique key to the hidden URL (which would associate with my email-address, giving the phisher a heads-up on its status), it leads to a form page made up to look just like one from Apple. The issue has been registered, apparently, because any attempt to call up the URL again leads to a forgery warning:

When I hit “ignore”, I get to an empty directory, so whatever the issue with the server was, it’s been taken care of.
Unfortunately, I didn’t take screenshots of the pages that were up, because they were shockingly well done - likely original HTML code from Apple’s website copied and used to make the Phish as believable as possible.
The first page asked you to enter your Apple credentials (Apple ID and password). This was followed by a form asking you to validate your payment information. This is where the fog in my brain was finally dispersed.
I immediately went to change my password for my Apple ID... you have to be VERY quick with this - if the Phisher is quicker, then you’ve lost your Apple ID to them. By the time you get it blocked, they’ve purchased all the musik, books and videos they need to entertain themselves for the next three years straight.
And here, I have to loudly criticize Apple: put yourself in my situation - you’re panicked. Your frantically trying to change your password. Go ahead, do the test. Put yourself in frantic mode, log onto the iTunes store and try to figure out how to change your password. Quick! Hurry! Too late...
Honestly, with the recent issues Apple had with iCloud - wether they are Apple problems or not - I would think security topics such as easy access to password changes or even to setting up two-factor authentication would be at the forefront of Apple management’s todo list.
Instead, even though I claim not to be an IT noob, I was unable to activate two-factor authentication without searching the web for instructions! And get this - you go to turn it on and... you have to wait three days! WTF, Apple? If I’m able to activate anything in my account, I already HAVE THE APPLE ID AND PASSWORD. Duh!!! Do you really think a three-day waiting period is going to make things more secure? I feel like I’ve applied for a divorce and the government is forcing me to think about my decision before concurring!
Steve, you went from us way too early!
Beware of Facebook Phishing
All,
a quick word of warning, as there is a new batch of Facebook-lookalike phishing mails being sent out:
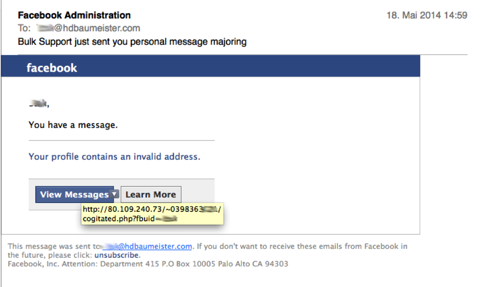
This is an attempt to - at the very least - verify your email address (in this case, it wasn’t the email address I use for my facebook account), possibly with additional attempts to gain details about your. I didn’t click on the button, so I couldn’t tell you what popped up... ;-)
Oddly enough, the sender didn’t try to mask the sending address; it came from directix@info.gamanetwork.com. Or perhaps it _was_ masked, though in that case I would have expected a service@facebook.com or similar...
Whenever you get an email with buttons like these - even if it really REALLY looks like it is from a legitimate source, always - ALWAYS - hover with your mouse over the button. Your mail software should show you the URL that button will call when clicked (if not, time to switch to something proper).
a quick word of warning, as there is a new batch of Facebook-lookalike phishing mails being sent out:

This is an attempt to - at the very least - verify your email address (in this case, it wasn’t the email address I use for my facebook account), possibly with additional attempts to gain details about your. I didn’t click on the button, so I couldn’t tell you what popped up... ;-)
Oddly enough, the sender didn’t try to mask the sending address; it came from directix@info.gamanetwork.com. Or perhaps it _was_ masked, though in that case I would have expected a service@facebook.com or similar...
Whenever you get an email with buttons like these - even if it really REALLY looks like it is from a legitimate source, always - ALWAYS - hover with your mouse over the button. Your mail software should show you the URL that button will call when clicked (if not, time to switch to something proper).
Phishing wird "intelligenter"
Die Zeiten von “I am the brother of the president of Nigeria” sind zwar nicht vorbei, dafür werden die Phishing-Betreiber “intelligenter” was die Aufmachung ihrer Emails angeht.
Heute ist diese Email bei mir angekommen:
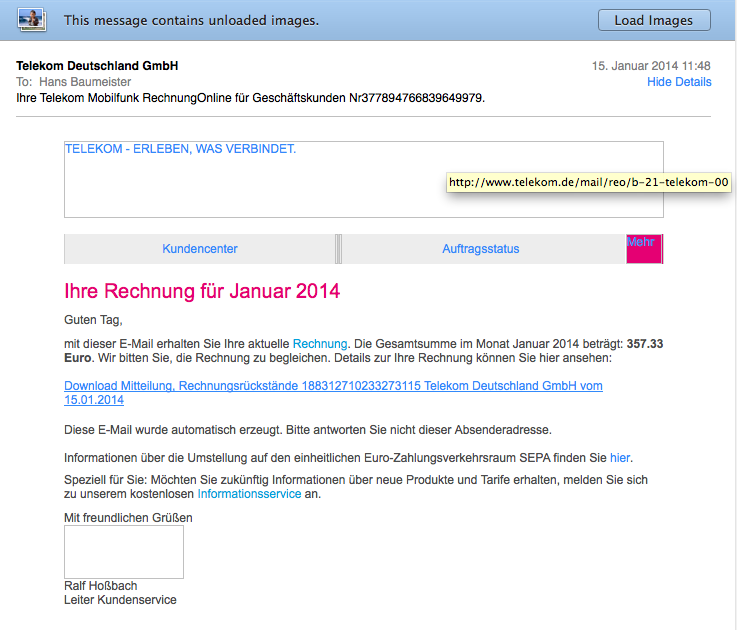
Ich habe explizit die Bilder nicht geladen, da in Bildaufrufen oft eine Kodierung versteckt wird, die Rückschlüsse wie eine Empfangsbestätigung ermöglicht. Zum anderen aber, um aufzeigen zu können, dass die Bilder tatsächlich von telekom.de gezogen werden (die gelb hinterlegte Anzeige kommt beim Mouse-Hover über dem Bild und gibt die Quell-URL an).
Lediglich der Link für den Download zeigt nicht auf die Telekom, sondern auf die URL http://581khg.nuusi.net/telekom/ (bitte nicht testen!!!).
Wäre ich Telekom-Kunde, hätte ich ggf. ungeprüft draufgeklickt. Um so wichtiger ist die Funktion, die jeder moderne Mailclient bietet: via Mouse-Hover sich ein Bild von der URL zu machen, die tatsächlich beim Anklicken aufgerufen wird. Oft werden nämlich http: URLs angegeben, hinter denen sich ganz andere URL’s verbergen.
Heute ist diese Email bei mir angekommen:

Ich habe explizit die Bilder nicht geladen, da in Bildaufrufen oft eine Kodierung versteckt wird, die Rückschlüsse wie eine Empfangsbestätigung ermöglicht. Zum anderen aber, um aufzeigen zu können, dass die Bilder tatsächlich von telekom.de gezogen werden (die gelb hinterlegte Anzeige kommt beim Mouse-Hover über dem Bild und gibt die Quell-URL an).
Lediglich der Link für den Download zeigt nicht auf die Telekom, sondern auf die URL http://581khg.nuusi.net/telekom/ (bitte nicht testen!!!).
Wäre ich Telekom-Kunde, hätte ich ggf. ungeprüft draufgeklickt. Um so wichtiger ist die Funktion, die jeder moderne Mailclient bietet: via Mouse-Hover sich ein Bild von der URL zu machen, die tatsächlich beim Anklicken aufgerufen wird. Oft werden nämlich http: URLs angegeben, hinter denen sich ganz andere URL’s verbergen.